Overview
On websites, we usually find features to do file upload. At the same time, file upload is one of the attacks of cyber security. We need to take care of our system, so that our customer feel satisfied and secure when using our applications.
In this page, we are going to do introduction to file upload attack and we will use Alibaba Cloud resources.
Prerequisites
- ECS
Implementation
We only need one instance ECS.
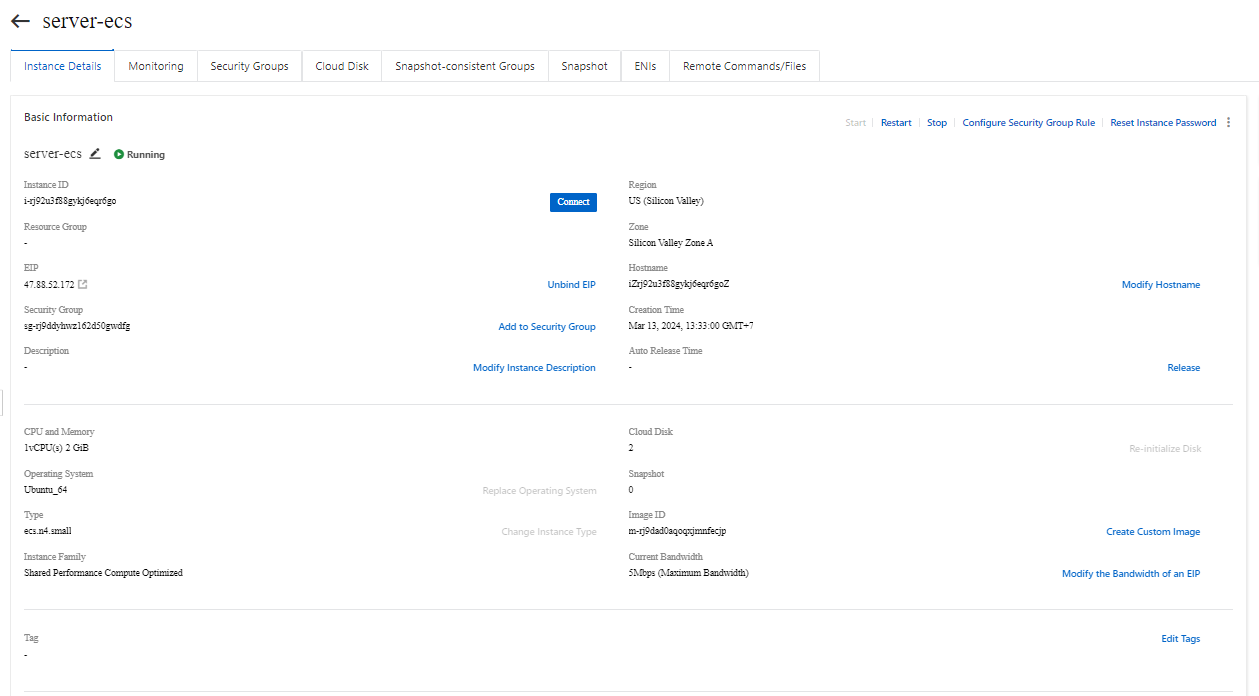
| Name | EIP |
| server-ecs | 47.88.52.172 |
It has simple website, there are few menu. In this menu, we just need to focus on “Upload Picture”.
Experiment 1
We use legitimate image as sample to upload.


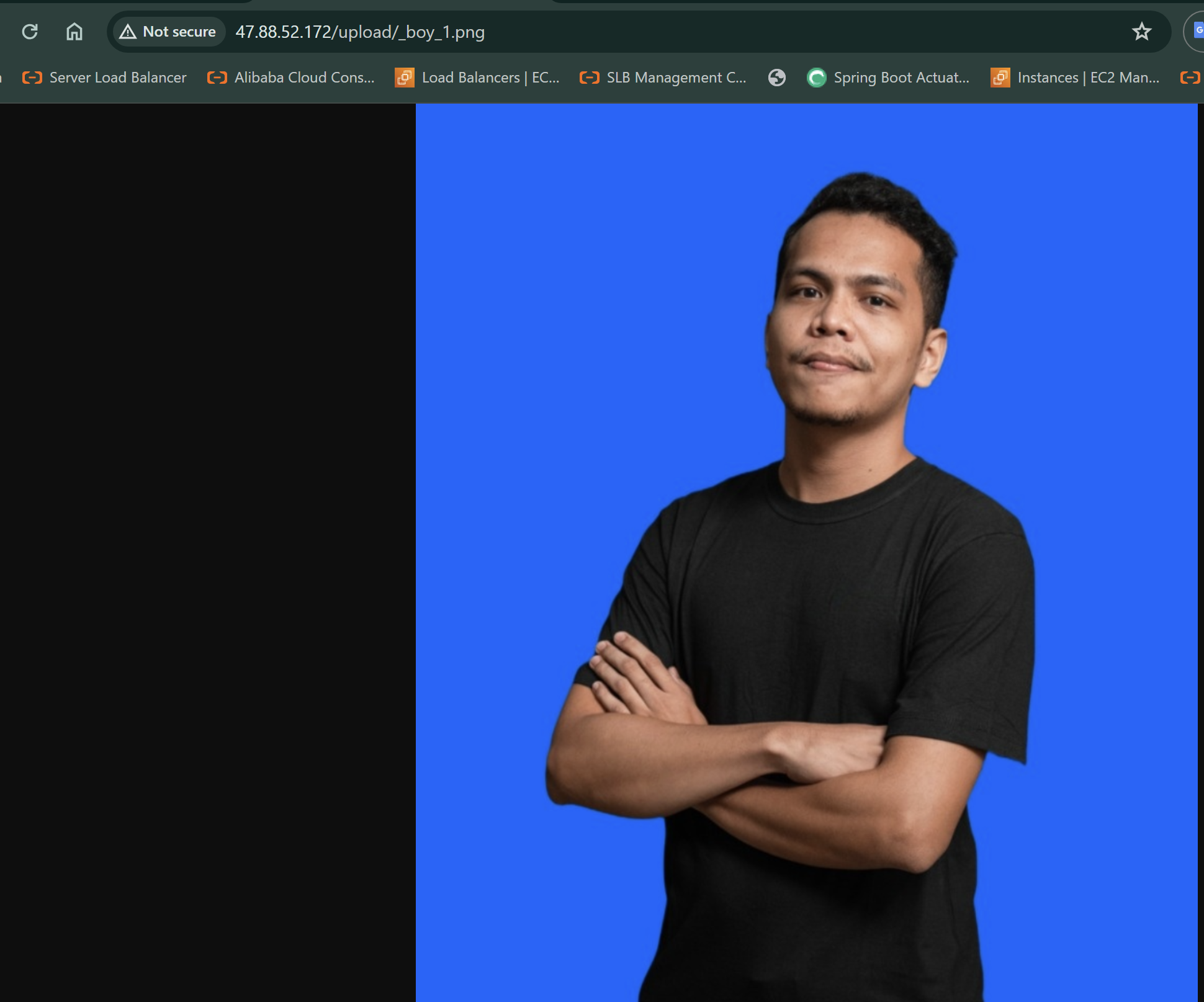
And our image can be loaded. Hmm? Looks suspicious.
Let’s try another experiment
Experiment 2
We try simple .php file named server.php
<?php phpinfo(); ?>And let’s try to upload.
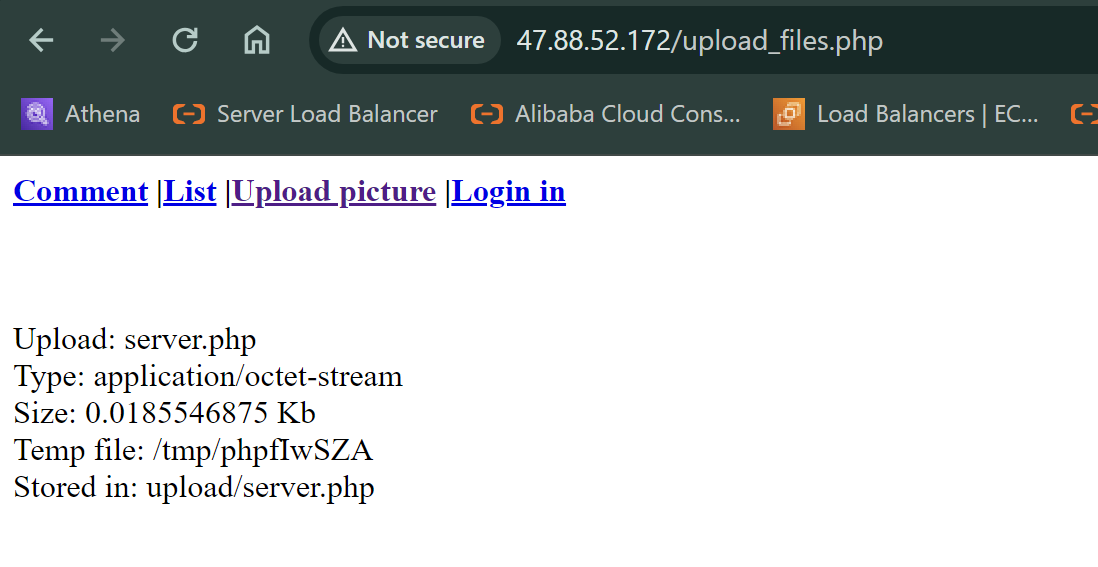
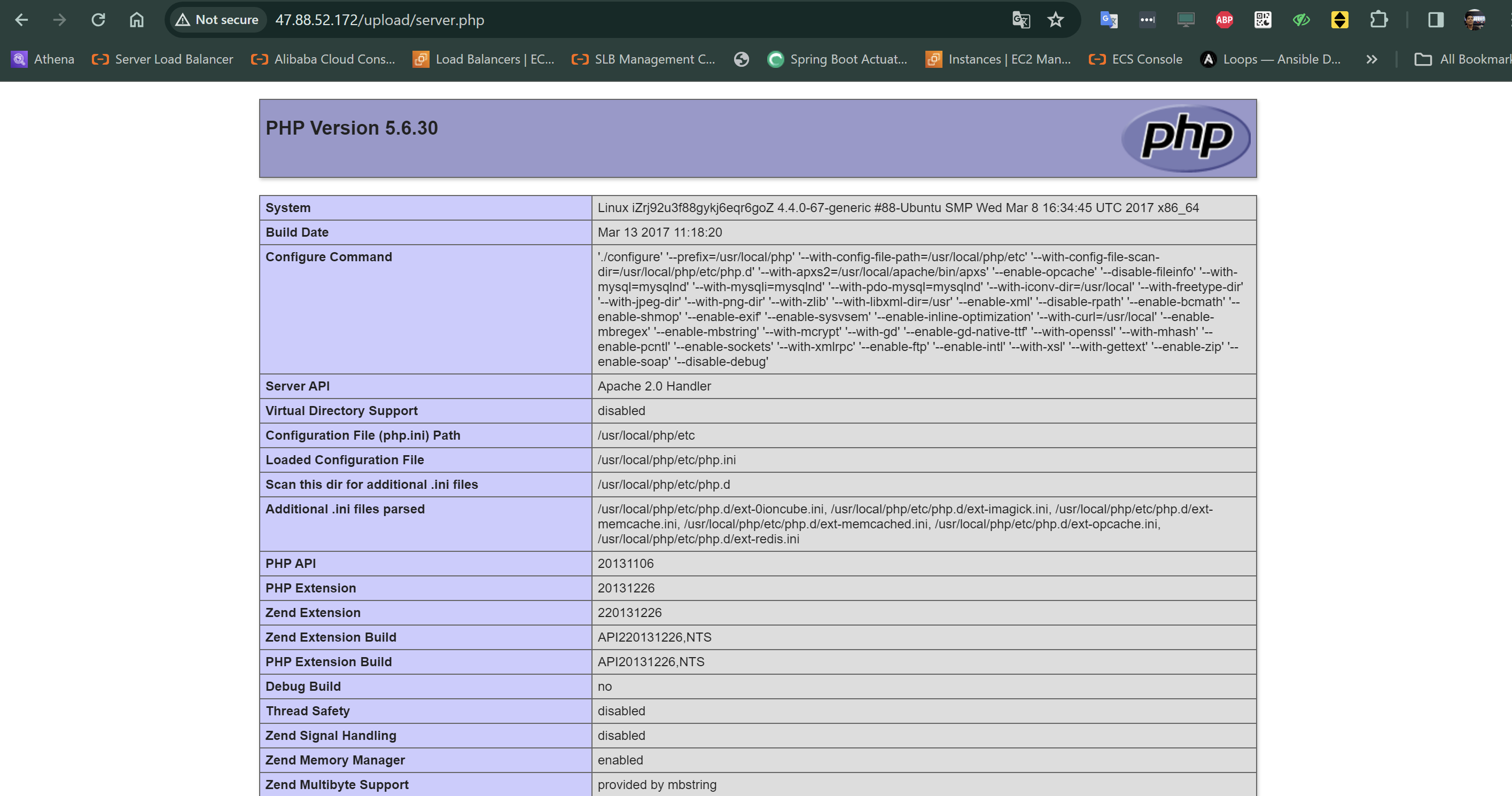
In this experiment, it results that it’s possible to see the version of php and other information. It looks so vulnerable.
Experiment 3
In the last experiment, i think we will use backdoor.
We will upload webshell, is it work or not? let’s try!
We will use b374k as webshell.

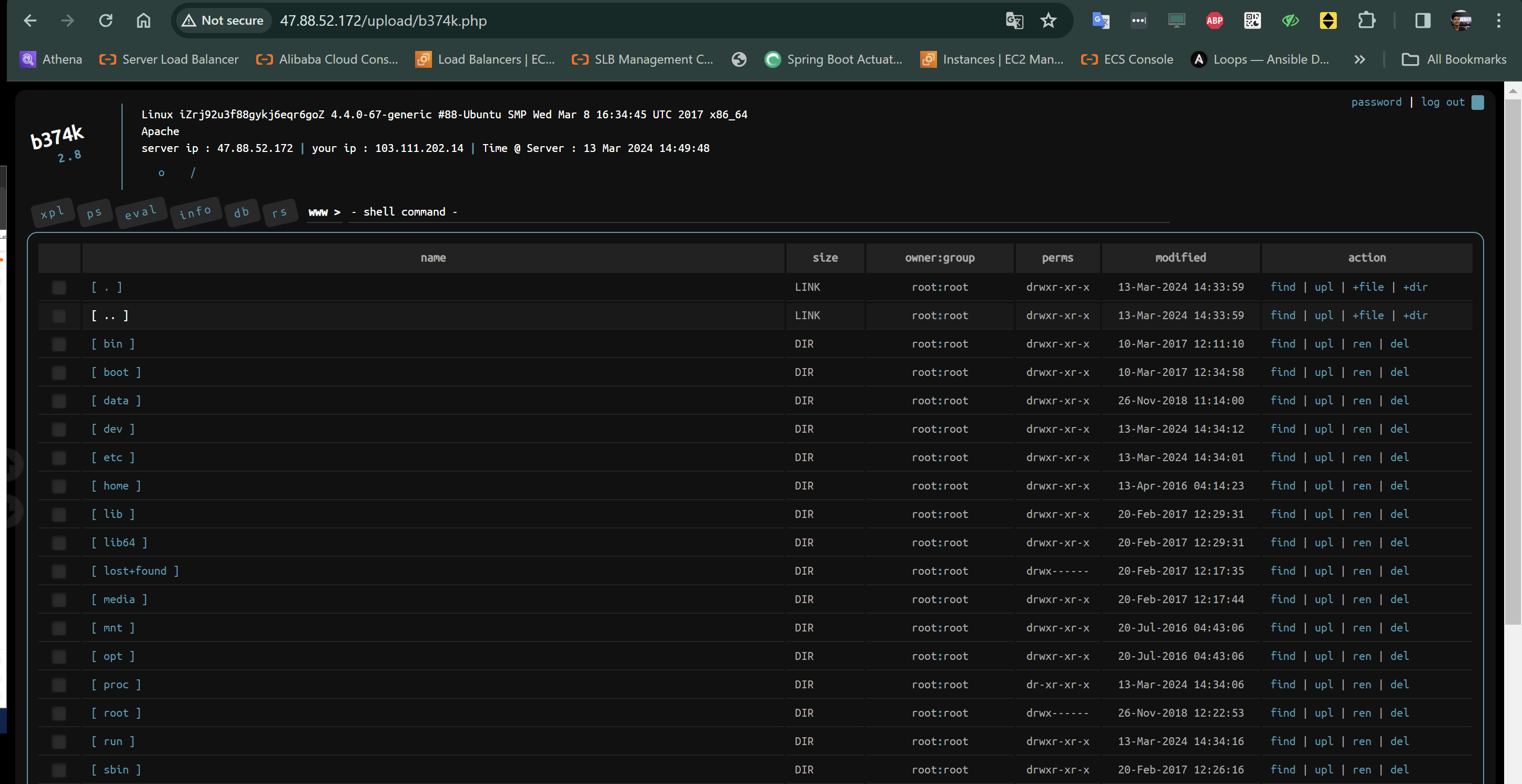
It shows that this “file upload” can be critical, because can load all directories included configurations, code, etc.
The suggestion is to set filter on extension of file, etc.
Reference
Labex.io

