Overview
Terraform is an open-source tool to do Infrastructure as a code.
It means that we will create resources by using this tool.
In this article, we are going to use Terraform to manage resources.
Let’s create the scenario, we want to create resources with this specifications.
- 1 VPC
- 1 Public Subnet (vSwitch)
- 1 Private Subnet (vSwitch which mounted to 1 NAT Gateway
- 1 Autoscaling Group on private subnet
– minSize 2 instances
– maxSize 5 instances
– scalingRule > 40% for CPU usage
To create these resources, we required AccessKey, SecretKey, and Terraform.
Implementation
Now, let’s start creating the resources.
We will create VPC first.
resource "alicloud_vpc" "vpc" {
vpc_name = "vpc-test"
cidr_block = "192.168.0.0/16"
}Then, we will create vSwitches to split the public and private subnet.
resource "alicloud_vswitch" "vswprivate" {
vswitch_name = "test-private"
vpc_id = alicloud_vpc.vpc.id
cidr_block = "192.168.0.0/24"
zone_id = "ap-southeast-5a"
}
resource "alicloud_vswitch" "vswpublic" {
vswitch_name = "test-public"
vpc_id = alicloud_vpc.vpc.id
cidr_block = "192.168.1.0/24"
zone_id = "ap-southeast-5a"
}Next. we need to add security group to provide the options when creating the instances.
resource "alicloud_security_group" "sgtest" {
name = "sg-test"
vpc_id = alicloud_vpc.vpc.id
}And dont forget to attach our private vSwitch to NAT gateway so that it can access the internet.
resource "alicloud_nat_gateway" "natprivate" {
depends_on = [alicloud_vswitch.vswprivate]
vpc_id = alicloud_vpc.vpc.id
specification = "Small"
nat_gateway_name = "nat-private"
payment_type = "PayAsYouGo"
vswitch_id = alicloud_vswitch.vswprivate.id
nat_type = "Enhanced"
}Since NAT Gateway have no EIP yet to associate with, we will need to add the EIP.
resource "alicloud_eip_address" "eip" {
}
resource "alicloud_eip_association" "eip_asso" {
allocation_id = alicloud_eip_address.eip.id
instance_id = alicloud_nat_gateway.natprivate.id
}I want to define ess_name with variable, but it can be optional based on your requirement.
variable "ess_name" {
default = "essscalingconfig"
}For the specifications, we want to use specifications like 1vCPU(s) and 4 GBs memory.
data "alicloud_instance_types" "in_types" {
availability_zone = "ap-southeast-5a"
cpu_core_count = 1
memory_size = 2
}Also, define the image that we use.
data "alicloud_images" "img_list" {
name_regex = "^centos_7_9.*64"
most_recent = true
owners = "system"
}After that, we will create config to add scaling group, scaling rule, and alarm.
resource "alicloud_ess_scaling_group" "ess_group" {
min_size = 2
max_size = 5
scaling_group_name = "${var.ess_name}"
removal_policies = ["OldestInstance", "NewestInstance"]
vswitch_ids = ["${alicloud_vswitch.vswprivate.id}"]
}
resource "alicloud_ess_scaling_configuration" "default" {
scaling_group_id = "${alicloud_ess_scaling_group.ess_group.id}"
image_id = "${data.alicloud_images.img_list.images.0.id}"
instance_type = "${data.alicloud_instance_types.in_types.instance_types.0.id}"
security_group_id = "${alicloud_security_group.sgtest.id}"
force_delete = true
active = true
}
resource "alicloud_ess_scaling_rule" "ess_rule" {
scaling_group_id = "${alicloud_ess_scaling_group.ess_group.id}"
metric_name = "CpuUtilization"
target_value = 40
scaling_rule_type = "SimpleScalingRule"
adjustment_type = "QuantityChangeInCapacity"
adjustment_value = 1
}
resource "alicloud_ess_alarm" "ess_alarm" {
name = "tf-Autoscaling"
description = "Alarming Autoscaling"
alarm_actions = ["${alicloud_ess_scaling_rule.ess_rule.ari}"]
scaling_group_id = "${alicloud_ess_scaling_group.ess_group.id}"
metric_type = "system"
metric_name = "CpuUtilization"
period = 60
statistics = "Average"
threshold = 40
comparison_operator = ">="
evaluation_count = 2
}As you can see above, from the config we will create resource Autoscaling Group with minSize=2, maxSize=5, it will trigger alert and scale the resource when the thresold on 40% of CPU Utilization.
The config will be merged in one file called main.tf.
We also need to add another file called provider.tf, but just fill the file with this config
provider "alicloud" {
}Because we use export AccessKeyID, AccessKeySecret directly from terminal.
And you can add version.tf to decide what version that you use for the terraform (based on compatibility)
terraform {
required_version = ">= 0.12"
}So the last thing that you need is only executing by
$ terragrunt applyAttachments
Directory structure
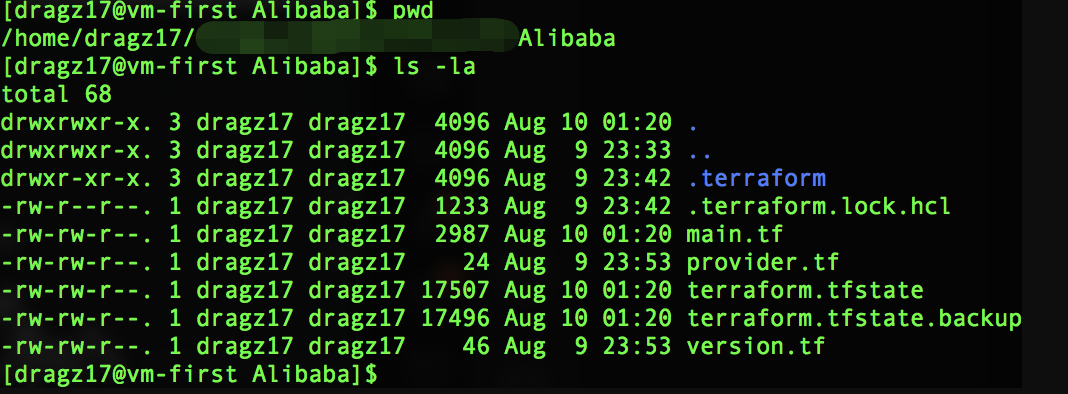
Export access key and secret key

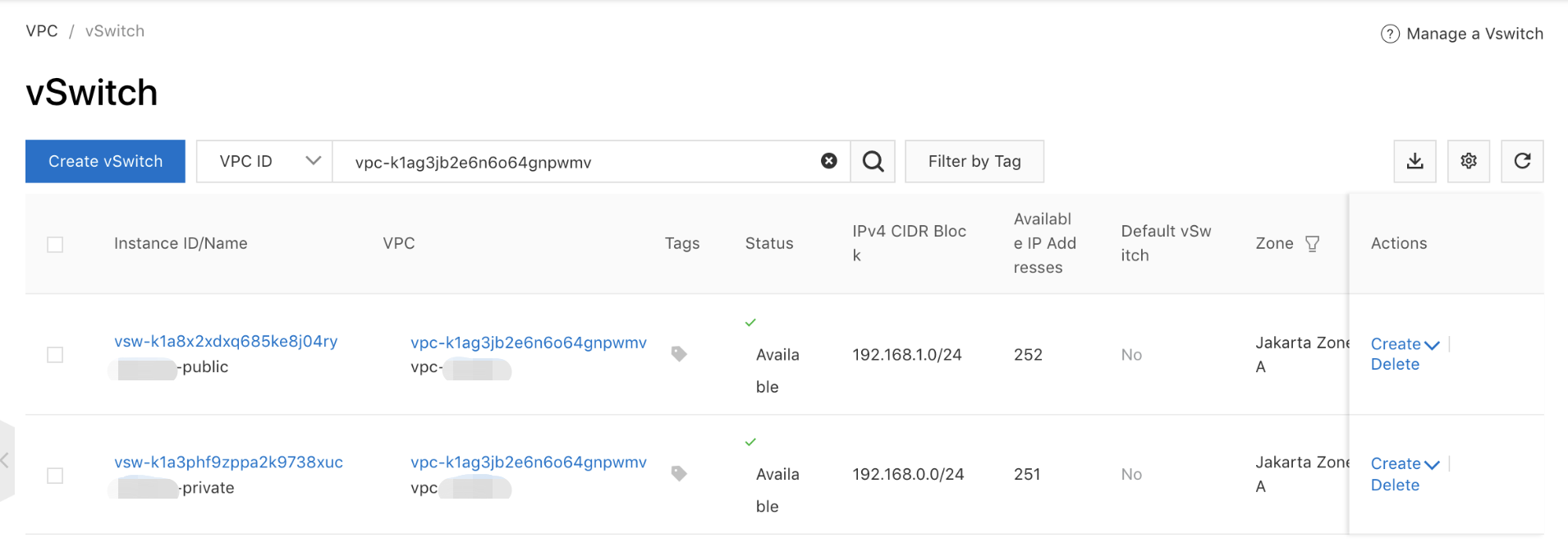
vSwitch Resources
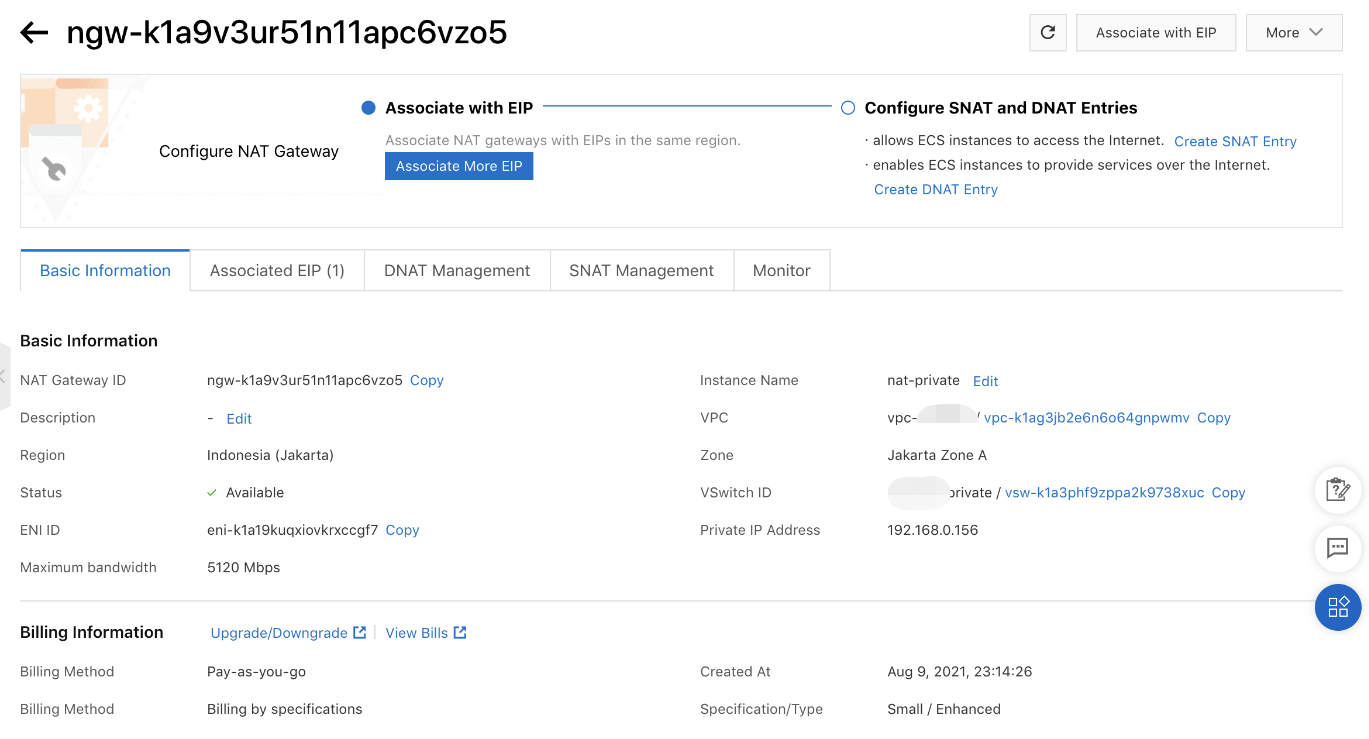
NAT to private vSwitch
Auto Scaling Group configurations

Auto Scaling rule
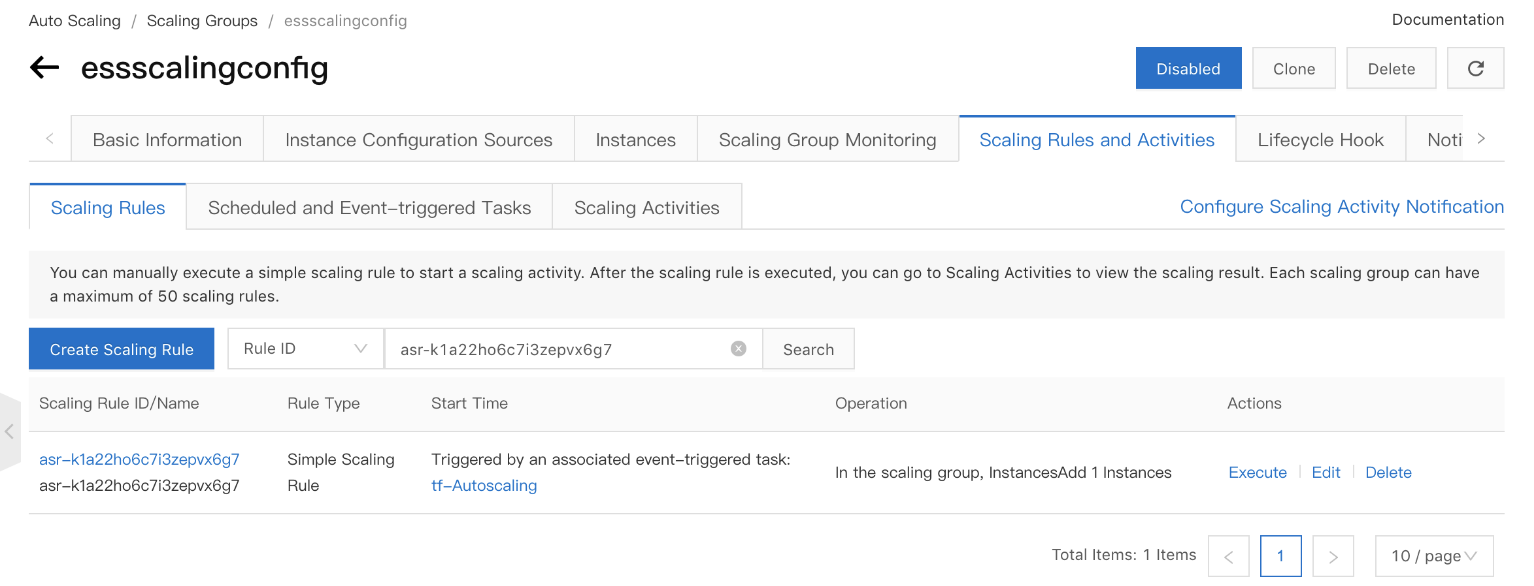
Event Triggered Task

