I am going to write my exploration with Traceback machine.
This is my first machine in Hack The Box (HTB).
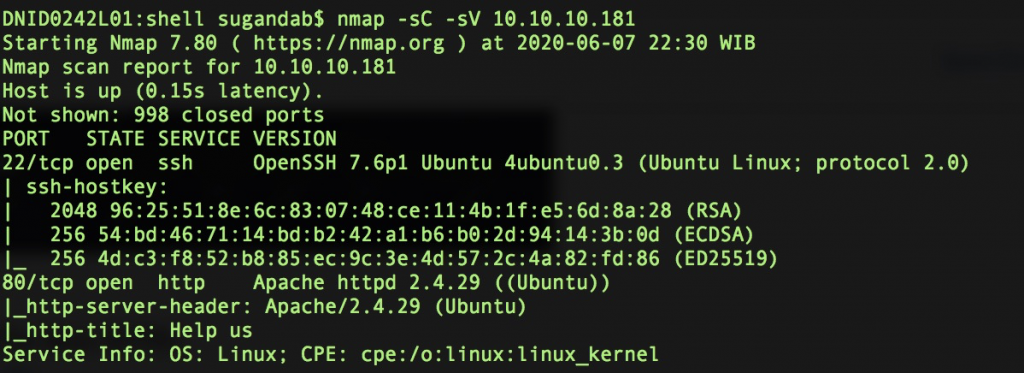
As usual, if we are given an IP address, we need to do port scanning to ensure the open-to-public port.
nmap -sC -sV 10.10.10.181Port 22 and 80 are open.
Let’s open via browser.

I think there is a backdoor inside.
Let’s check the source code.
A clue…

Let’s take attention on commented lines.
“Some of the best web shells that you might need”
If you are going to search it from Xh4H, it will redirect you to the top one, because Xh4H fork it from the top one.
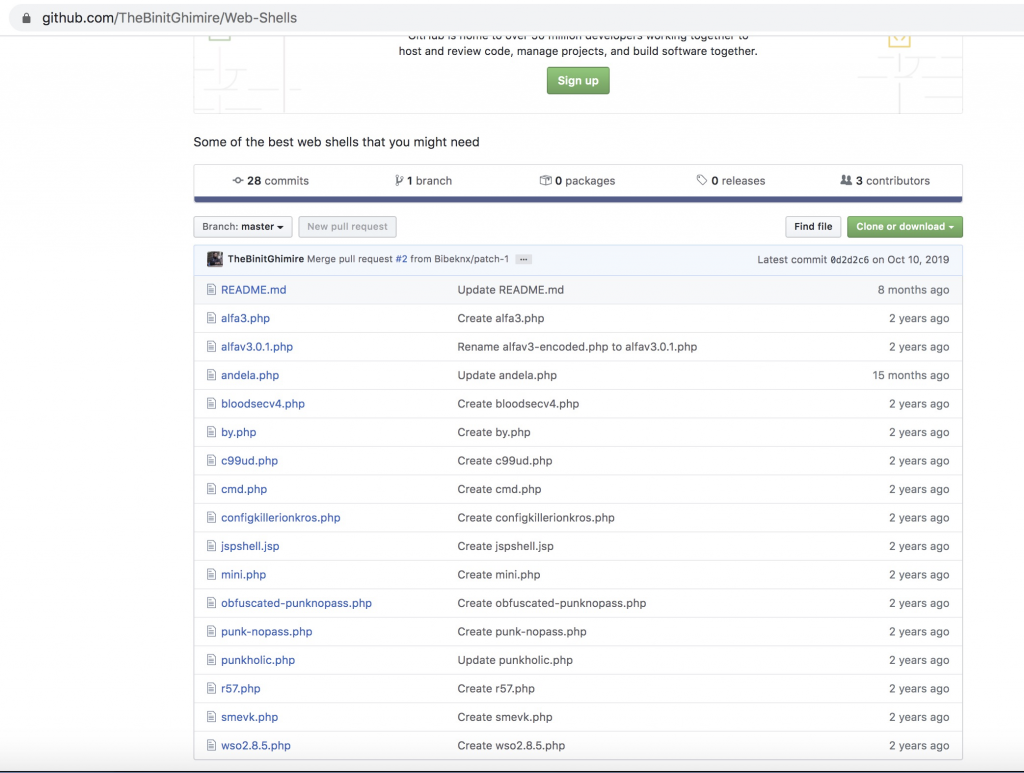
So many versions of shells here. You can try to predict if one of them exist on the machine (10.10.10.181). Let’s use brute-force directory.
gobuster -w list-shell.txt --url 10.10.10.181
smevk.php existed, next take a look on smevk.php file.

Go to 10.10.10.181/smevk.php
Username:Password = admin:admin
We are in.

To make you can ssh, you need to transfer your public key inside the machine. Copy your public key and store it in /home/webadmin/.ssh/. Why not /home/sysadmin/.ssh too? Because you can’t go there. Let’s escalate from the thing that you can.

Welcome, you already inside machine as webadmin.

Let’s see files inside directory.
There is a “note.txt”.

Hmm, seems not good with this clue.

Let’s check the syntax that can be executed by webadmin.
sudo -l
Then try to go as sysadmin.
But before go there, we need to try to understand “lua” and “luvit”.
Lua is programming language, and luvit is one of lua code implementation.
Let’s check the shell of lua on GTFOBins.
From GTFOBins, you can try this exploit.
lua -e 'os.execute("/bin/sh")'Ok, let’s try it as input for changing account to sysadmin
sudo -u sysadmin /home/sysadmin/luvit

As i know, /bin/sh is better used on macOS, and /bin/bash on linux.
Ok, we owned user flag.

Let’s go to root.
When we are going to ssh, you can see that we have custom header. I reference you to this web, just for knowing the location of the welcoming file. It’s located in /etc/update-motd.d.
echo "id" >> /etc/update-motd.d/00-headerLet’s try to ssh again to webadmin (open new terminal).

Wow, it’s running as root.
I try to know what is inside root directory.
echo "ls /root" >> 00-header 
There is single file, root.txt.
We just need to cat the file now by using file 00-header.

We owned the root flag.
Traceback Machine already been owned.
I’ll post this after the machine was expired.
Please inform me if the writeup was exposed by (someone).
Written on June 07th, 2020.


